Ransomware Attacks Map chronicles a growing threat
In May, Allan Liska, an intelligence analyst at the cybersecurity firm Recorded Future, published research that caught the attention of security analysts and government officials everywhere. It included a list of 169 different ransomware attacks against state and local governments dating back to 2013, but that were now cropping up at an alarming rate.
Many government officials had already keyed into the ransomware threat, but Liska’s research lent new insight to just how broad, aggressive and increasingly common this type of malware had become. Workers at state agencies, municipal districts and grade schools are waking up to find that their computers have been locked and data encrypted by viruses with names like SamSam and WannaCry, as perpetrators in remote countries demand ransoms ranging from hundreds of dollars to millions.
Now there are new high-profile incidents every few weeks: Baltimore; Riviera Beach and Lake City, Florida; 23 communities in Texas, while smaller events, many of which go unreported, strike almost daily.
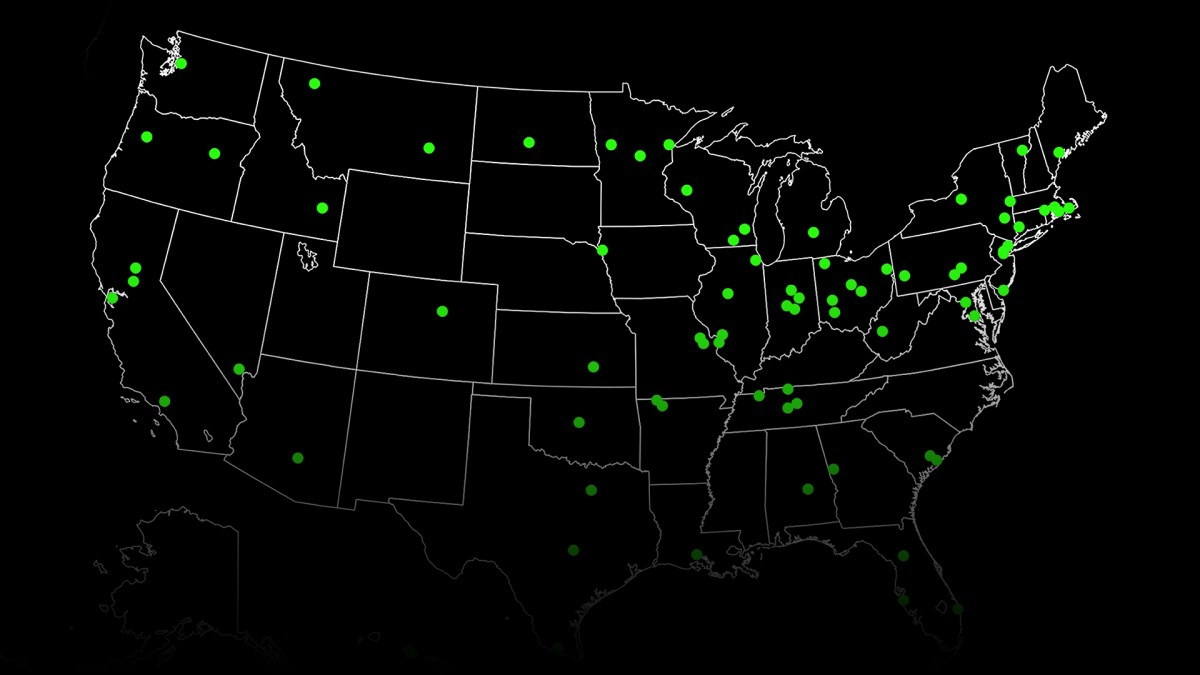
In an attempt to keep track of these incidents, StateScoop has developed an interactive map of every known public-sector ransomware attack going back nearly six years. Beginning with Liska’s original set of 169 attacks, StateScoop’s reporters and designers have continued to track new attacks, plotting out targets and cataloging the type of malware used, the ransom demanded and whether or not the victim paid up.
Click here to open the map in a larger window.
Upon release, the map contains data for 245 ransomware attacks, but new dots will be added as new attacks are reported. In an interview with StateScoop, Liska predicted there will be plenty of new data to add in the coming months.
“Right now, it appears to be getting worse,” he said.
New vectors, new worries
More than 100 public-sector ransomware attacks have been reported in 2019 so far, compared to 51 reported in 2018. Liska gave several reasons for the quickened pace. One that’s caused grief among IT leaders is that hackers are shifting their sights from specific governments — say, a city like Atlanta, which suffered a crippling SamSam infection in March 2018 — to the managed service providers that many smaller communities use to supply their tech needs. Hit a service provider, and a sophisticated ransomware virus can filter out to many customer organizations that haven’t employed sufficient protections.
“It’s an attack model that’s gaining interest and one we expect to be repeated going forward,” Liska said.
An attack in August that hit 23 local governments in Texas — as well as one in July that affected several public school systems in Louisiana — were both delivered through MSPs. At a Department of Homeland Security summit on cybersecurity last month outside Washington, analysts and officials tried to understand what the new method means for government.
“While it’s a new item, it’s really no different than what we’ve seen in ransomware for a few years,” said Ben Spear of the Center for Internet Security, a nonprofit that that helps governments share information on cyberthreats. “The MSP [vector] is just a growth of that based on the scale of a single provider.”
But hacks of service providers are not the only emerging worry. In August, the Cybersecurity and Infrastructure Security Agency, the DHS unit responsible for protecting the United States from cyberattacks, warned that state and local election officials — still on edge from Russian government hackers’ attempts to tamper with voting systems in 2016 — present appealing targets for ransomware that could be used to disrupt voter-registration databases or the websites that report unofficial tallies on election nights, especially in the smallest jurisdictions where IT teams are tiny and resources are scant.
“We’ve got 113 counties with fewer than 15,000 residents, and most of those election offices are one person,” Texas Elections Director Keith Ingram said at the DHS conference. “Our mandate is to help those election officials do what they need to do: help draft policies and procedures, buy the equipment to segment their networks so election systems are as protected as they can be from a more general attack.”
‘You don’t get a pass’
The advice and support that Ingram talked about isn’t much different than the common prescription offered to protect local-government functions writ large: install security patches regularly, run vulnerability assessments and store system backups offline.
Despite dozens of publicized ransomware attacks that tend to be accompanied by that advice, the message doesn’t always take. In the case of Texas’ ransomware attack in August, state CIO Todd Kimbriel said last week that the 23 communities affected were hit because of lax protections on their ends, not their common service provider’s.
One reason that small towns suffer ransomware attacks so often is that they struggle to keep up with the pace of technological growth. But that’s not an excuse, said Gary Buonacorsi, chief IT architect for the cybersecurity firm Tanium’s state, local and educational practice.
“We have so many more types of things to attack, from our laptops and mobile phones and servers, to [internet of things] devices, and then you’ve got the sprawl of the network,” he said. “You can’t have an endpoint out there. Whether it be a phone or laptop, you just can’t do it. Whether you’re small or not, you don’t get a pass.”
Big cities can fail to prepare for ransomware just as easily as the small ones, though. In Baltimore, where a virus called RobbinHood encrypted several municipal systems on May 7 in hopes of a $76,000 payday, the recovery has been peppered with embarrassments for the city’s IT department. There was the discovery of a risk assessment that called Baltimore’s aged network infrastructure a “natural target” for cyberattacks. An audit found IT workers had been saving backups of critical data on their local computers, which were later corrupted by the ransomware. And CIO Frank Johnson eventually admitted that his department lacked an incident-response plan.
Baltimore officials expect their ransomware attack will ultimately cost taxpayers $18 million, while Johnson, once the city’s highest-paid employer, is out of a job.
Buonacorsi said local governments can be particularly vulnerable when politics balkanize municipal agencies into uncooperative fiefdoms.
“You have those silos, and I think that is what’s the barrier for change,” he said. “To me, it’s as much the fault of a city council as it is of IT. IT can bring a problem to bear, but if you don’t have a funding source or your legislating body doesn’t realize it’s a problem, I don’t think it’s fair to just blame IT.”
Ransomware plans help
There are a few ransomware success stories. One newly popular model at the state level is to follow practices similar to those used in hurricanes by getting the governor to declare a statewide emergency. Some states’ emergency management agencies, which have playbooks to manage manpower and resources during critical events and can call in other agencies to assist, have started revising their plans to include cyberattacks.
Colorado was the first to invoke an emergency declaration in March 2018, when its Department of Transportation was hit with the SamSam virus. Louisiana followed suit last summer when several of its school districts were under attack, as did Texas when it marshaled its response to the multi-city incident. In all three cases, teams that included IT workers, state police, National Guard members and other partners were able to mitigate the bulk of the damage in a matter of weeks, officials in all three states have said. But they are still the exceptions rather than the rule. The National Governors Association said in July that many states still lack formalized cyber disaster plans.
And in Orange County, North Carolina, a March ransomware attack resulted in newfound appreciation for cybersecurity across an entire 1,300-person government.
“It forced us to adjust and change some of our processes, and I don’t just mean the IT organization,” Jim Northrup, CIO for the county of about 145,000 residents, told StateScoop. “I mean the county as a whole. In the past, people would complain about changing passwords. Never did I think I’d hear customers saying ‘Make our passwords stronger.’”
While Northrup said his county is still dealing with some of the aftereffects, it’s well past the “firefighting mode” it was in when the ransomware knocked out employee emails, public-building Wi-Fi and housing vouchers. His office is also preparing to hire its first-ever chief information security officer, a position Northrup said he’d clamored for in the past without luck.
“Without sounding too unprepared, we’re kind of waiting for the next one to happen,” he said. “And everyone should be in that mode. Are we ready? I think the past event has gotten us closer to ‘yes.’”
‘We’re seeing an explosion’
Even with government organizations becoming more attuned to the threat, ransomware is evolving in ways that make it more unpredictable. Instead of hackers choosing their target selectively — as in the cases of Atlanta, Baltimore or Colorado DoT — some of the newest strains of ransomware use a software-as-a-service model. Aspiring cybercriminals can launch an attack by paying a hacker group for a license to use a virus similar to how an enterprise would subscribe to Office 365.
“We’re seeing an explosion in the underground of ransomware-as-a-service,” Liska, the Recorded Future analyst said. “You’ll see on a number of hacker forums, they’ll basically advertise their services. Now anyone with a couple hundred dollars can launch a ransomware campaign. You don’t have half a dozen to a dozen groups. You have hundreds.”
Liska said Sodinokibi ransomware (which also goes by the name REvil and has been associated with multi-city Texas attack), is one of the more common ransomware strains being sold on hacker forums. It’s believed to be the successor to GandCrab, whose creators claimed to have netted $2 billion through the as-a-service model in just 15 months.
Ryuk, another common virus that’s frequently delivered via banking trojans designed to corrupt financial data, is not as commonly sold as a service, Liska said. But its designers, believed to be based in Eastern Europe, are trading on the six-digit payouts they’ve received from communities that include Lake City, Florida, and LaPorte County, Indiana.
“In forums, they’ll talk about how this city in Florida paid $400,000,” he said. “It doesn’t matter overall that state and local governments are less likely to pay [than businesses], what matters is that there’s big numbers.”
These tactics, combined with the increased attacks on managed service providers and persistent understaffing in local governments, promise a map that will soon become more crowded with dots.
“You used to have some level of skill,” Liska said. “Now these campaigns are moving to low-barrier and no-barrier models. It’s an attack model that’s gaining interest and one we expect to see repeated going forward.”
StateScoop’s Ransomware Attack Map was developed by Komi Akoumany, Mike Hilario, Danny McGarvey and Colin Wood.