Oregon advances CIO’s office toward cybersecurity unification with new law, advisory council

A new Oregon cybersecurity law unifies information security efforts across all state agencies and establishes a cybersecurity advisory council hoped to improve coordination during cyberattacks.
SB 90, signed into law June 29, will “transfer agency information technology security functions, employees, records and property to the office of the State Chief Information Officer no later than January 1, 2018.” The law codifies the language from an executive order signed In September by Gov. Kate Brown designed to shore the state’s defenses against cyberattacks and protect the state’s data and “aging information technology infrastructure.”
The law also establishes the Oregon Cybersecurity Advisory Council, which consists of nine state-appointed public and private sector cybersecurity experts. The council will serve as an advisory body to Chief Information Security Officer Stefan Richards and state Chief Information Officer Alex Pettit, and serve as a forum for cybersecurity policy discussion throughout the state.
Eventually, Pettit and Richards also plan to create an additional Oregon Cybersecurity Center of Excellence to serve as a “public-private state-civilian interface for information sharing, coordination of cyber incident response, developing a statewide cyber strategy, identifying best practices and encouraging development of Oregon’s cyber-security workforce,” said Sean McSpaden, principal legislative IT analyst at the Oregon Legislative Fiscal Office.
Pettit told StateScoop the new law is a move to apply a community healthcare model to the world of cybersecurity, in both the state’s private and public sectors.
“Just like a community, when one of us has measles, then everyone is going to be at risk for measles unless someone, somewhere makes sure that everyone has their inoculations up to date, and we can identify it quickly and take care of it and that we can make sure that we have the right practices in place to keep everybody else from getting infected by it,” Pettit said.
A failure to communicate
The new law can be traced back to several incidents that found offices unprepared to rally a defense or properly coordinate.
“We’ve had a couple of instances where we’ve had small, local governments that attach to the state government in various ways, one of the biggest ways being law enforcement by way of the criminal justice information system,” Richards said. “So we own the one and only connection for the state to the federal government for that kind of information, so we network it to all the law enforcement entities in the state.”
When one of those entities was thought to have been breached, Richards said, there was no structure in place to inform the technology agency that help was needed. The issue of communication surrounding IT infrastructure isn’t one that Pettit and Richards are taking lightly.
“We have that very real problem, and that’s a lot of what started us down this road,” Richards said. “Hey, we’re not operating just as state government — the organism really is the whole state and we need to inoculate all parts of it, and this really gives us the ability now to deploy our resources, should we need to.”
Before Pettit and Richards could tackle statewide IT problems, however, they had to handle their own.
“[Prior to SB 90,] Each agency would sort of attach onto the state network and then build out from their on their own,” Richards said. “Modernization, the equipment, the software, hardware choices from the network were completely left to the agencies.”
The unification of previously agency-specific information security functions as outlined by the new law will alleviate the communication issues, Richards says.
“What this is, at least for security, is … we have access and expertise in a central fashion to try to disseminate to every agency, even those that didn’t have staff, to get a common level of hygiene or inoculation across the whole enterprise, instead of just those that are rich enough to afford it,” Richards said.
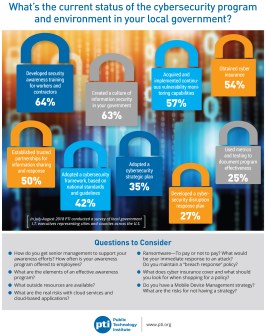
An assessment of cybersecurity preparedness last year found that risk assessment and risk management strategies were absent in many agencies, Richards said.
“Actually dealing with things in a risk-prioritizing fashion versus buying something from TV or that you read about in the Wall Street Journal last week or whatever the latest press is … was universally a problem,” Richards said.
A life of its own
Shoring up agency cybersecurity is only half of the aim of the new bill, however. In order to set up the Cybersecurity Center for Excellence — which Pettit envisions as a 503C organization they will establish someday — Pettit and Richards must first present a business plan to the state legislature.
The advisory council is a stepping stone, Pettit explained.
“So what we’re doing is taking those leaders from our already-established group and putting them in voting roles to [advise] state government … like, ‘Here’s how your unified security should look and here’s how you should prioritize,’ but also, ‘Heres some priorities for Oregon as a whole and here’s how we would structure it.”
Richards added that this body would help drive funding for research to understand which offices around the state are most vulnerable.
While the state is in charge of appointing members to the advisory council, Pettit and Richards said they don’t intend for the state to influence their decision-making.
“The cybersecurity excellence center is meant to have a life of its own,” Richards said. “We actually are looking at the advisory council as the state not even being in a voting chair, with the nine chairs being filled by people in the community and the state not even have a voting role.”