Someone is selling VPN access to a city government in Arizona

A regular user of underground forums and illicit online marketplaces with a track record of selling stolen credentials that can be used to access government, university and corporate networks is attempting to sell access to systems belonging to a large city in Arizona, the cybersecurity intelligence firm GroupSense told StateScoop.
The user, who is believed to be based in either Russia or Ukraine, wants $30,000 for access to a VPN portal hosted on the city’s .gov domain, which would grant access to local internal network resources and enable the buyer to carry out spearphishing efforts to lay groundwork for ransomware or another type of cyberattack against a range of government departments, including those that deal with public safety or critical infrastructure.
“City resources include City Court System, City Government, Police Department, Fire Department, Recreation Services, Engineering Services, Utility Services, Library, Fleet Services, Airport, Finance, Street Maintenance, Animal Control, Human Resources, Legal, Information Technology,” reads a screenshot of the user’s forum post that GroupSense shared with StateScoop. “You will receive domain user crews. I will provide the domain admins email address for privilege escalation/spearphishing.”
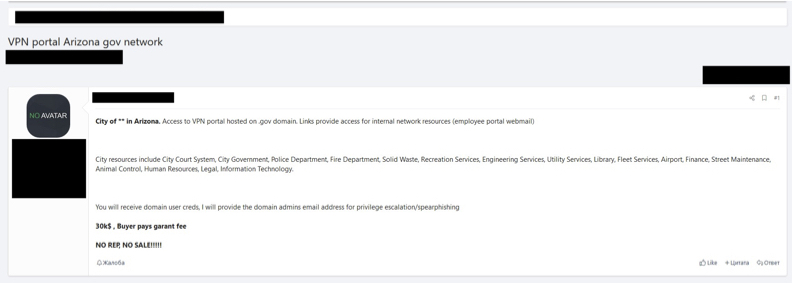
A screenshot of an underground hacker forum shows a user attempting to sell VPN credentials for a city in Arizona. (GroupSense)
Bryce Webster-Jacobsen, GroupSense’s director of intelligence operations, said in an interview the company has not figured out what city is being targeted, though it has ruled out Phoenix. There are several other cities in Arizona big enough to fit the description of what the credential seller is offering, however.
He also said the seller is an experienced member of the illicit websites where hackers gather to buy and sell tools and is highly rated by previous buyers, not dissimilar to how sellers on legitimate online marketplaces like eBay and Amazon are reviewed.
“They have a pretty good reputation, above-average reputation,” Webster-Jacobsen said. “The fact that the user is prevalent on multiple forums with same persona is an indicator to us they’re not just trying to scam people.”
He added that the seller has been active for at least a year-and-a-half, and has made previous sales of stolen credentials that precipitated ransomware attacks, including some against universities. But the city government credentials would be this user’s biggest score yet.
“We see a range of a few thousand dollars to a couple others in the $14,000 to $17,000 range,” Webster-Jacobsen said, noting that universities tended to represent the higher end of that range. “I would imagine [$30,000] is because they have more access to more parts of the city. The two unique departments are airport and city court. Those are not prevalent in every city in Arizona.”
He described the seller as a middleman in the cybercriminal economy, obtaining network credentials and then selling them in turn to other actors who carry out attacks like ransomware. In the past, the seller has expressed interest in obtaining logins to Amazon Web Services and licenses for Cobalt Strike, a legitimate penetration testing tool that is also popular with hackers.
Webster-Jacobsen said GroupSense is attempting to identify the city so it can notify officials there that their network has potentially been compromised. He also said the fact that the VPN credentials being sold could access so many systems related to public safety, transportation and utilities is particularly concerning in light of the recent hack of a local water treatment system in Florida.
“There have been many conversations about security of critical infrastructure,” he said. “It doesn’t necessarily start with someone hacking into the control panel. It will often start with this rudimentary run-of-the-mill government access and then a threat actor can work their way through the network.”






