‘Smart’ parking meter vendor had data stolen in ransomware attack

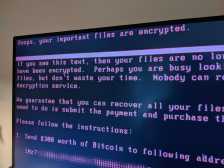
A company that sells “smart” parking meters and technology used by parking-enforcement agencies in cities around the world was recently the victim of a ransomware attack that also exposed some of its internal files on a website maintained by the hackers responsible.
CivicSmart, a Milwaukee firm that sells parking meters capable of processing mobile payments, hardware and software used in enforcing parking rules and mobile apps used by motorists and government employees alike, was hit last month with a form of ransomware known alternatively as Sodinokibi or REvil. Messages posted to a website on which the hackers name their victims and leak stolen files in an attempt to elicit ransom payments suggest that CivicSmart paid an unspecified amount to have its files decrypted.
The attack was noticed in March by the Israeli security firm Under the Breach, but otherwise went undisclosed. A screenshot of the hackers’ site — titled “Happy Blog” — suggested that they were preparing to publish as much as 159 gigabytes of data taken from CivicStart. A text file shared with StateScoop revealing the names of stolen file folders indicates the data may include employee records, contracts with cities and parking-garage vendors, bank statements and credit card numbers of people who paid to park using CivicStart’s products.
The hackers’ page for CivicStart was later updated to indicate the company had paid up and the stolen files were taken down.
“CivicStart are very pragmatic guys and real businessmen, who managed to admit core mistakes and fix all the vulnerabilities,” it reads. “Be like CivicSmart, try not to get into this blog :).”
Along with the hardware and software it provides to parking authorities, CivicSmart also integrates its systems with popular mobile apps that drivers use to feed the meter, including Parking Panda and ParkMobile. And just because the company’s stolen data was removed from the “Happy Blog,” CivicSmart’s customers remain at risk for further cyberattacks and other fraudulent activity, said Brett Callow, an analyst at the cybersecurity firm Emsisoft.
“The problem in cases like this is that the criminals still have the data,” he told StateScoop in an email. “They may claim it will be deleted upon payment, but why would criminals ever delete information they may be able to further monetize?”
[ransomeware_map]
REvil emerged as one of the more pernicious forms of malware last August when it was used to knock 23 Texas communities offline simultaneously. The hackers behind it have since shifted their tactics to publish files stolen from victims in an attempt to shame them into payment, following a trend popularized by the hackers behind the Maze ransomware, who published files belonging to the City of Pensacola, Florida, last December. The City of Torrance, California, suffered a similar attack last month at the hands of another ransomware variant, though officials there originally denied a data breach had occurred.
Callow said CivicStart’s stolen files could be used to leverage spearphishing attacks against city agencies to infect them with ransomware, or rip them off with business email compromise schemes. He pointed to another recent REvil attack that targeted Brooks International, a professional services firm, that revealed information belonging to a Canadian paper manufacturer, which was itself then hacked.
“In short, incidents should be disclosed so that the affected customers/cities can be on high alert,” Callow said.
But whether CivicStart has informed any of its government or enterprise customers is unclear. Reached by phone, the company’s chief executive, Mike Nickolaus, said he was “not in a position to confirm or deny” the cyberattack or whether he has informed his clients.