Verizon data breach report offers 10-year look at cyber-crime
 A decade of data breach information has revealed an unprecedented level of insight into the trends and patterns of cyber-crime, including industry-specific trends that for the first time can be mapped to 14 critical security controls.
A decade of data breach information has revealed an unprecedented level of insight into the trends and patterns of cyber-crime, including industry-specific trends that for the first time can be mapped to 14 critical security controls.
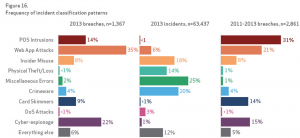
According to an advance copy of Verizon’s 2014 Data Breach Investigations Report, obtained by FedScoop, 49 organizations from 95 countries contributed data on more than 63,437 security incidents, including 1,361 confirmed data breaches. That’s a huge increase from the 19 contributors representing just 27 countries in last year’s report.
“It’s a really good sample of what’s going on in the world,” said Stephen Brannon, a principal with the Risk Team at Verizon. During the last 10 years, Verizon has collected and coded data on more than 100,000 security incidents.
But the 2014 report represents a significant departure from past years. It not only includes incidents that did not necessarily lead to a confirmed data breach, but it maps the incidents to nine basic attack patterns. It then maps those attack patterns to specific industries and makes specific recommendations based on the SANS Institute’s Critical Security Controls list.
The 10 years of data included in the report reveals nine overall threat patterns. But for the first time, Verizon researchers have been able to map those specific threat patterns to specific industries, enabling executives in those industries to make better decisions about what security technologies to purchase.
Among the most problematic trends identified in the report was the significant increase in the number of external hacker threats that organizations now face.
“The number of internal and partner actors has stayed steady and external actors have been increasing year over year,” Brannon said. “There are definitely insiders and partners that you have to worry about, but by the numbers there are a lot more people outside the organization perpetrating security incidents.”

Perhaps more troublesome is the gap between the time it takes these attackers to steal data and the time it takes organizations to discover the incident. “Attackers are a lot faster than defenders. And the gap is actually widening,” Brannon said. “That’s probably where we as an industry need to focus our resources.”
In contrast, the percentage of organizations that are able to detect incidents on their own without relying on third-party researchers and contractors is falling.
“That’s low, it’s staying low and may be getting lower,” Brannon said. “That’s an area where industry really needs to improve a lot.”
Although the media have spent an inordinate amount of time in 2013 discussing major data breaches involving retail stores and point-of-sale attacks, the Verizon data breach report shows that POS attacks continue to trend downward since 2011. Industries commonly hit by POS intrusions are restaurants, hotels, grocery stores and other brick-and-mortar retailers, where intruders attempt to capture payment card data.
“While POS breaches have been in the headlines lately, it is not indicative of the actual picture of cybercrime,” according to Verizon.
Cyber-espionage is up again, according to the 2014 report, representing a four-fold increase compared with the 2013 report. But the 511 incidents included in this year’s report is also partially due to a bigger dataset, according to Brannon. In addition, these attacks were found to be the most complex and diverse, with a long list of threat patterns. As it did last year, China still leads as the site of the most cyberespionage activity; but the other regions of the world are represented, including Eastern Europe with more than 20 percent.
Human error was among the most common causes of data loss and privacy breaches in the public sector. According to the Verizon data, “misdelivery” — sending paper documents or emails to the wrong recipient — is the most frequently seen error resulting in data disclosure.
“One of the more common examples is a mass mailing where the documents and envelopes are out of sync (off-by-one) and sensitive documents are sent to the wrong recipient,” the report states. “A mundane blunder, yes, but one that very often exposes data to unauthorized parties.”Follow @DanielVerton






