Phishing campaign spoofs local-government websites to rip off small businesses

A foreign hacker has been running a phishing campaign that uses phony versions of local government websites in the United States, targeting small and medium-sized businesses in those communities to steal personal credentials, cybersecurity firm Lookout told StateScoop.
In the phishing scheme, the hacker has sent messages luring victims to replicas of web pages that cities and counties use to register potential vendors. Victims are drawn in by what appear to be solicitations to bid on local-government contracts, said Jeremy Richards, the Lookout researcher who has been tracking the scheme.
Recipients who take the bait are directed to “near-perfect mirror[s]” of those sites equipped with registration forms designed to steal personal information, including names, phone numbers, addresses and Social Security or employer identification numbers. The phony forms appear near identical to those on the governments’ real websites, though the URLs used — information-center.us, for example — are not government domains.
After completing the forms, users are then sent to a phishing kit designed to resemble a Microsoft login page where they are prompted to enter an email address.
Among the government websites that have been imitated are those belonging to San Mateo, California; Tampa, Florida; North Las Vegas, Nevada; and Dallas County, Texas.
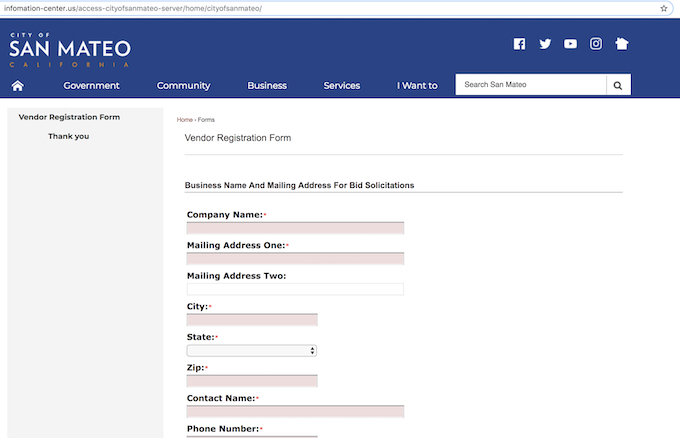
A phishing campaign page mimicking a San Mateo, California, government website. (Lookout)
Lookout, which is headquartered in San Francisco, detected the campaign while investigating domains used as command-and-control systems for malware that targets Microsoft Windows systems. Richards said the hacker believed to be responsible has been known to cybersecurity researchers since at least 2015, but that the local-government scheme only started in February. Previously, the attacker was known to target users of streaming media services.
“This particular actor has been operating out in the open for about four years and they haven’t really been protecting their trail,” he said. “This is brand new for us. But it’s brand new for him as well.”
Richards said it’s also possible this attack is the work of a small group of hackers, but that it’s likely a single person considering the relatively slow speed of the campaign, which spoofs one municipality every few weeks rather than several simultaneously.
While Richards could not cite any direct evidence that any government employees fell for this particular scam, he said the hacker has “definitely” been successful in recent years. Richards said Lookout was able to link the hacker to an Instagram account that features posts of custom cars and expensive computer parts.
The company traced the recent attack to a Facebook profile mentioning an elementary school about 20 minutes from where the hacker is believed to be located. Richards declined to name the country where the hacker is believed to reside, however, citing the possibility that the Facebook page is a fake.
Imitating a local-government website is a particularly insidious form of cyberattack given the relatively high levels of public faith in local and state governments. A Gallup poll last September found that 72 percent of adults trusted their local officials a “great deal” or “fair amount,” compared with 42 percent for the federal government.
Phishing efforts often impersonate recognizable and trusted brands — like Microsoft — to lure in victims, but the government angle amplifies that effect, according to Richards.
“Impersonating a local government also lends a of lot credibility phishing attacks—especially since its targets may be unfamiliar with local government sites,” he wrote in his research.
IT officials in Tampa, Dallas County and other governments listed in Lookout’s report declined to answer StateScoop’s questions about whether they were aware their websites had been spoofed or if they had taken any measures to warn their business communities.






